Blog Runas Command
Runas command and other run as administrator options on Windows 10
Run an application with elevated rights as administrator on an UAC System and
run an application with administrator rights from a normal standard user account are
two different problems.
Find explanation, solutions and examples for both problems and a better understanding on this page.
Run an application with elevated rights as administrator on an active UAC system
What are elevated privileges?
- Elevated rights are needed from a program, batch file or other scripts, to get access to system relevant settings. This can be folders, registry entries, hardware and other windows system setting.
- An administrator has no elevated privileges on an UAC activated system, until he confirmed a warning message from the User Access Control (UAC).
- This UAC Dialog is only shown, if the program request elevated system rights or the administrator do it for the application, by mouse right click and select run as administrator.
How can i request elevated privileges?
- The application request elevated privileges within the program source code, so the developer of the progam request the privileges
by UAC program manifest level asInvoker, highestAvailable or requireAdministrator.
Microsoft docs UAC manifest level - An administrator can also request elevated permissions manually, by right click on the application.exe and select in context menu >> run as administrator <<
- An application can be configured to run with elevated privileges for a specific administrator, by setting the compatibility property >> run as administrator <<
- There is a free portable tool RunElevated, which can request elevated rights for an application, batch file or any other script
and for all users on the system by the easy call >> RunElevated.exe YourApplication.exe <<
or drag YourApplication.exe and drop it onto RunElevated.exe
How can i get elevated privileges and bypass the UAC?
- Disable the User Account Control UAC and all administrators work now with elevated permissions in all applications without UAC dialog.
- Download the tool RunAsRob and start program with system account via the login option as system.
https://runasrob.com/RunAsRobRunAsAdminAsSystem.html
System account knows no UAC and has more rights than an administrator. The account has access to backup directories, user profiles and all other system folders and settings.
RunAsRob, with login option as system, is an effective and flexible method for a copy job, monitoring, installation procedures of programs, updates, patches or drivers.
It is not suitable if you need the settings of a user account in the running application, like printers, shares or program settings, because the system account is not a full user account with a user profile. - Use the predefined local account administrator. It is the only account which bypass the UAC on an UAC activated system.
You just have to enable this account and in some Window versions you have to set additional the registry key
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\SystemFilterAdministratorToken to 0 >> SystemFilterAdministratorToken
Run an application with administrator rights from a normal standard user account
Why do i need to run an application as administrator from a limited account?
- Delegate specific administrator tasks to specific users or a user group.
- Enable to install an authorized software from a normal user account. This can be an application, an update, a driver or any other installation package.
- Allow a standard user to change any specific system setting.
- Authorize a copy job, a backup job or a monitoring job which need system rights, to run it as normal user.
- Some programs need administrator rights for a lot of different reasons and you want to use it without beeing an administrator.
- Enable working as administrator only when it is necessary and not regualary.
An administrator should not work with an administrator account by default, because it is a high risk he do a fatal mistake unconsciously in his daily work.
This security setting is a rule from linux since unix exist and microsoft implement this with User Access Control UAC. I see no other reason in the UAC than avoiding that administrator work as administrator.
If you don't work as administrator by default and just using the administrator account when you have to change explicit something on the system,
you can deaktivate the UAC and work from a limited account and use runas utilities to do the specific administrator job.
How can i run an application as administrator from standard user account?
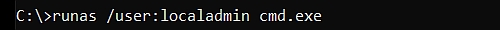
Command runas from Microsoft
>> runas /user:admin c:\windows\system32\cmd.exe <<
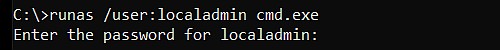
Next step you will be asked for password of the administrator account
-
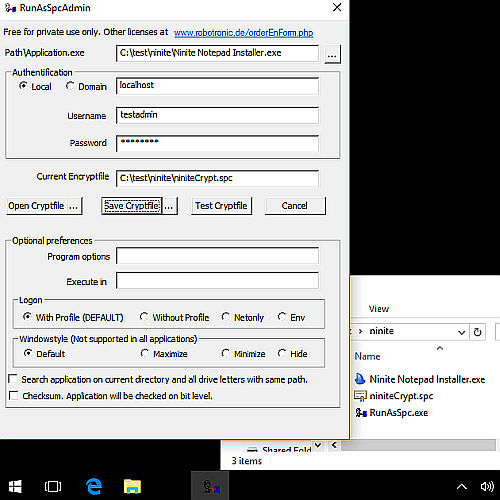
Command runasspc including password argument
>> runasspc /user:"admin" /password:"pass" /program:"c:\windows\system32\cmd.exe" <<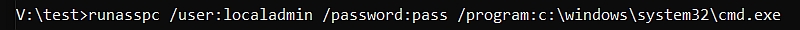
Runasspc can also hide the password in an encrypted file.
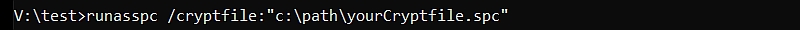
You find RunAsSpc on https://robotronic.net/runasspcen.html -
Runasrob, the most effective tool with different possibilities for any purpose.
Grant the allowed directory in the graphical user interface RunAsAdmin, a part of RunAsRob, then you can call this allowed application by command via runasrob.exe
>> "C:\Program Files\RunAsRob\runasrob.exe" "C:\Windows\System32\cmd.exe" <<
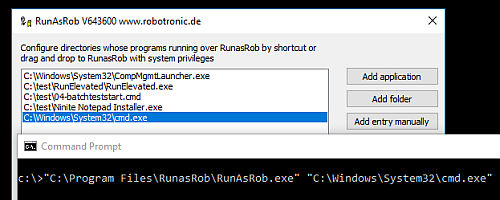
RunAsRob can call the allowed application with system account and bypass the UAC Dialog
or as administrator with full profile of the calling user, because he will be an administrator with his own account, only for the authorized application.
It is not necessary to store administrator credentials anywhere.
You can authorize one or more applications, you can use wildcard in the path name and you can grant folders. Read more about RunAsRob on https://runasrob.com -
Other tools. Please take a look on https://runas.eu
Examples to run an application as administrator from standard user
Packages of Ninite Installer can install by a limited user without to know the administrator credentials
1) with RunAsRob the part RunAsAdmin
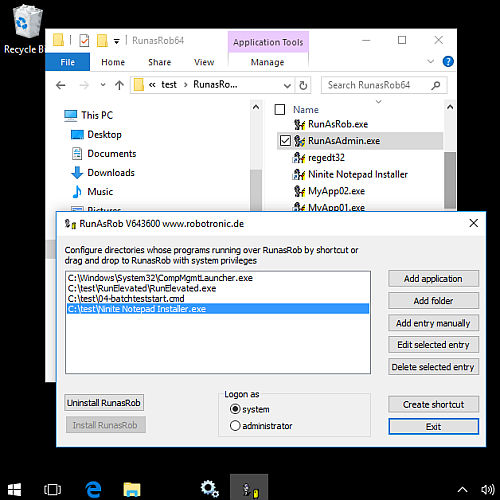
2) or RunAsSpc with administrator login information of administrator in plain text
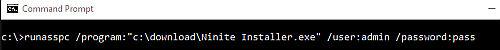
3) or RunAsSpc with encrypted file and hidden paassword.
Run Powershell script as administrator
First of all, enable powershell script on machine.
- launch C:\Windows\System32\WindowsPowerShell\Powershell.exe from with elevated privileges by right click run as administrator,
- write command >> Set-ExecutionPolicy remotesigned << or >> Set-ExecutionPolicy unrestricted <<
Now there are various ways.
1) Run script as administrator from admin account with elevated privileges.
- Self elevate powershell script is working, by call the same script with elevated privileges inside the script. I am against doing this, because it is the risk to get an endless loop
- or elevate the powershell script by calling the script via another powershell start script, which elevate the main script.
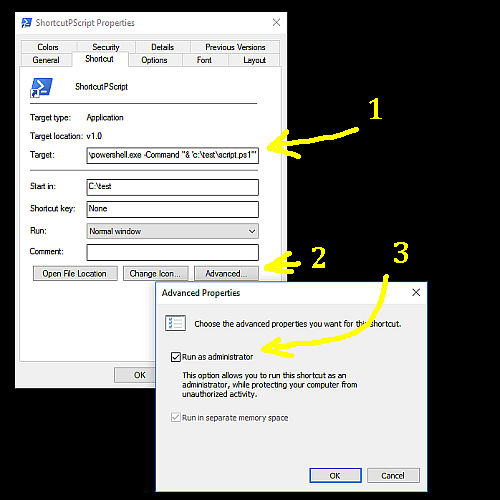
>> Start-Process powershell.exe -ArgumentList '-file c:\test\powershell\pscript.ps1' -Verb RunAs << - or create a shortcut to your Powershell script with command PowerShell.exe -Command "& 'C:\Temp\script.ps1'"
and set in the shortut property tab -> Advanced -> Run as administrator
2) Run script as administrator from standard user account.
- Create a shortcut to your Powershell script with command PowerShell.exe -Command "& 'C:\Temp\script.ps1'"
and set in the shortut property tab -> Advanced -> Run as administrator
After start of shortcut, you will be asked to enter administrator credentials. -
An elegant way to run Powershell script as administrator from standard user and avoid entering the credentials and bypass the UAC is using RunAsAdmin from RunAsRob.
You just have to authorize the script in RunAsAdmin and launch it via RunAsRob.
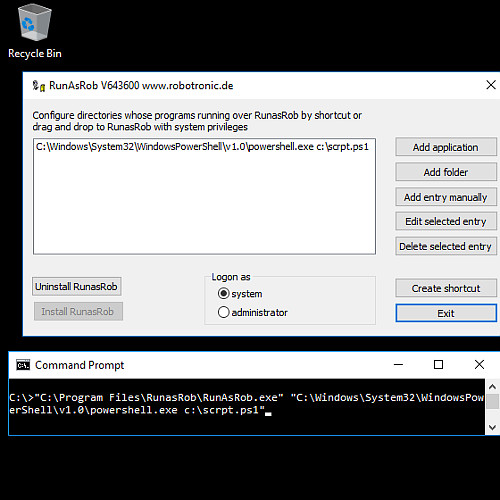
See following example configuration with a Powershell script >> c:\scrpt.ps1 <<- Authorize the complete call in RunAsAdmin >> C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe c:\scrpt.ps1 <<
- with login option >> as system <<
- Now you can call scrpt.ps1 via RunAsRob and it is running with system rights under standard user account.
>> "C:\Program Files\RunasRob\RunAsRob.exe" "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe c:\scrpt.ps1" <<
Run cmd as administrator to get the command line with elevated privileges
Run command line with elevated privileges from administrator account.
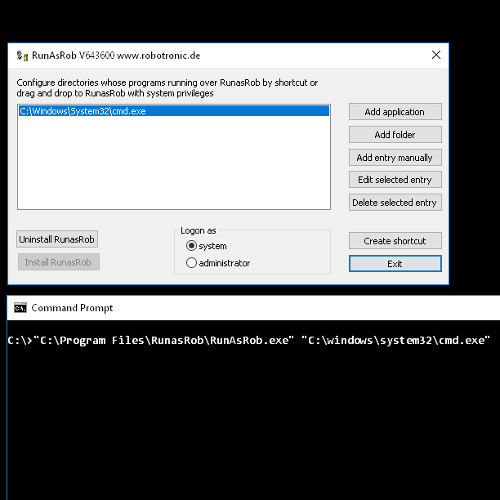
- It is known you can right click cmd.exe and select in context menu >> run as administrator <<
- To run cmd as admin directly by double click to avoid a right click and first select the option >> run as administrator << , create a shortcut to cmd.exe and set in the properties of the shortcut -> advanced -> >> run as administrator <<
Run command line with elevated privileges from user account.
- use a shortcut to the cmd.exe you have set in the properties -> advanced -> >> run as administrator <<
after double click on shortcut you will asked for the credentials of an administrator - If you don't want to enter credentials each time use RunAsSpc
>> runasspc.exe /program:"c:\windows\system32\cmd.exe" /domain:"localhost" /user:"admin" /password:"pass" << - If you want to hide the credentials use RunAsSpc with an encrypted file >> runasspc.exe /cryptfile:"c:\tmp\launchCommandLineAsAdminEncrypted.spc" <<
- If you want to hide the credentials and bypass the UAC use RunAsRob, the part RunAsAdmin
and allow cmd.exe to run as administrator from user
Run batch file as administrator
Launch a batch file with elevated privileges from an administrator account.
Create a shortcut of the batch file, select in properties of the shortcut -> advanced -> run as administrator.
Start a batch file as administrator from a user account.
Choose the easiest way and use RunAsRob https://runasrob.com
- Allow the directory of the batch file in RunAsAdmin, a part of RunAsRob
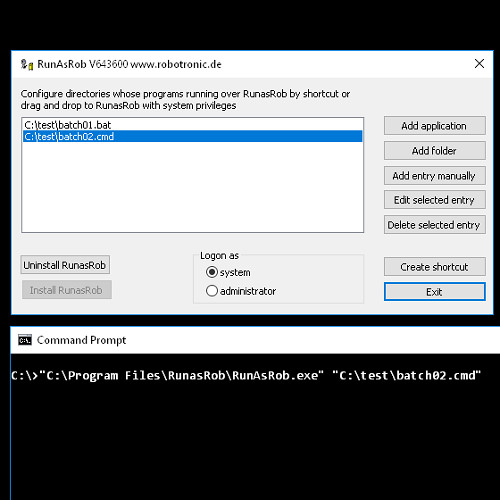
- Start your batch file with command >> "C:\Program Files\RunasRob\RunAsRob.exe" "C:\test\batch01.cmd" <<
- Call this command directly, in a batch file, any script or in a shortcut